As the plant floor becomes more connected, ensuring proper cyber protections for industrial control systems (ICSs) needs to be a priority for manufacturers. By understanding your organization’s cyber posture and making the right tools available as part of a well-thought-out ICS cybersecurity strategy, the necessary groundwork can be put in place to combat detrimental cyber incidents that interrupt operations, cost money, and impact physical safety.
All too often, our engineers come across companies that are knee-deep in a cybersecurity implementation project yet not in agreement on what they are working towards. This generally happens because the project’s OT stakeholders were not involved in the development of the organization’s cybersecurity program. Therefore, key stakeholders are not aligned on critical parts of the program including cybersecurity standard selection, scope of applicability, agreed-upon interpretations, and acceptable and unacceptable alternative controls.
To avoid these issues, it is best to perform a foundational cyber posture evaluation prior to engaging in any cybersecurity projects. If current and desired cyber posture are clearly defined first, stakeholders can work together to generate actionable and effective implementations that will reduce the risk of a cybersecurity incident.

Three Steps to Properly Evaluate Your Current Cyber Posture and Establish Your Target Posture
Based on our experience working on cyber posture assessments with customers across various industries, there are three key steps to properly performing a cyber posture assessment:
- Information Gathering – This includes collecting any potentially pertinent documented and non-documented information, including any regulatory requirements that must be met. The purpose of this phase is to identify what information exists and to assess the broad quality of any documentation.
- Establishing Current Cyber Posture – This step allows you to identify the appropriate starting place for implementing effective changes that will reduce cybersecurity risks. This involves two parts – using the findings from the information gathering phase to then review the current policies and strategies in place, how these policies are being implemented, and what gaps may exist and then developing a consensus on your organization’s current cyber posture.
- Identifying Target Cyber Posture – This phase involves an analysis of the potential impact to business functionality from both internal and external threats and from intentional as well as unintentional actions to establish the appropriate target posture.
Taking the appropriate steps to achieve your target posture is critical because cyber threats do not remain static, and neither does the OT landscape. As shown in Figure 1, cybersecurity is an ongoing process that needs to have staying power. This means your organization needs the right goals, tools, and support to stay effective. Once you have a target cyber posture, you can effectively take the correct action to stay abreast of these outside forces.
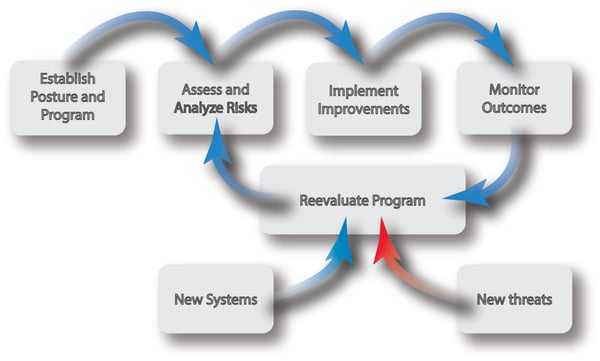
Figure 1. ICS Cybersecurity needs are dynamic and constantly evolving, but having an established cyber posture makes it easier to continually make improvements to protect your ICS from potential threats.
Working with an ICS Cybersecurity Expert to Evaluate and Improve Your Cyber Posture
Since evaluating your organization’s cyber posture is an involved process where it is helpful to have objectivity, it is a good idea to contract with an expert consultant such as ACE. Our engineers can collaborate with your organization to conduct a best practice assessment and host a workshop that focuses on the end goal of implementing the right standards and strategies to get your organization where you want it to be. We encourage a collaborative process, and unless the customer asks us to, we are not going to bring in a predefined set of standards and explain how the organization is failing to meet those standards.
In the end, we believe that actionable activities are the result of effective planning. By starting with a properly executed cyber posture assessment, your organization can develop the most effective cybersecurity strategy and get ahead of potentially detrimental cyber threats before they develop.
Learn more about assessing your organization’s cyber posture by downloading our white paper, Cybersecurity Success Starts with Understanding Your Organization’s Cyber Posture.




